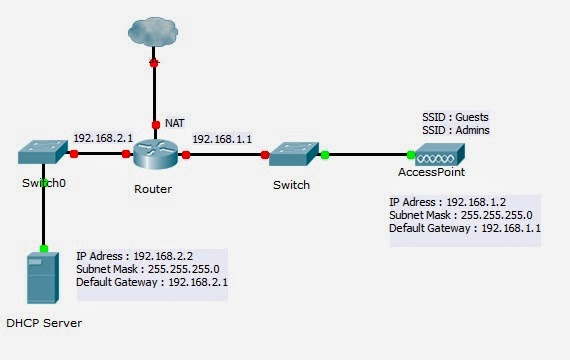
The network below is a simple network without any access control list on the access point or any firewall rules on the router.Furthermore , the access point using WPA2 Enterprise with Radius Server Also if you want a cheaper option instead you can use Ubuntu server which is an open-source and free of charge OS.
This network using :
Router : Vyatta Router
Access Point : Cisco Access Point
Server : Windows Server 2008
Switch: Cisco Switches
**Servers and Access Points always using STATIC IP Addresses for many reasons:
- Easy identifying the server.
- Able to get access to the server any time using the same IPaddress.
- Able to apply any firewall rules related with your server's ipaddress.
- You don't want your servers to changing IPaddress all the time because many configurations have to change along with that.
Configuration Files
Access Point
The first step is to configure your access point with a static IP address.
You only need to configure the BVI of the AP but you need to assign a default gateway as well as the AP need to send packets to the Radius Server.
AP# configuration terminal
AP(config)# int bvi1
AP(config)# ip address 192.168.1.2 255.255.255.0
AP(config)# ip default-gateway 192.168.1.1
AP(config)# no shut
AP(config)# end
AP# write memory
In the next step you only need to access AP
1) Access AP's GUI with its IP address and upload the settings.
2) Use tftp server to upload the settings. (
Backup/Restore Cisco Config File)
Also you can edit the settings to set your own SSID, IP addresses and host name.
Cisco AP Config file
------------------------------------------------------------------------------------------------------------
!
version 12.3
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname AP
!
enable secret 5 $1$0hB5$Kzg8JBh2wFsa2kuLkjZX/1
!
led display alternate
ip subnet-zero
ip domain name wirelesserver.com
!
!
aaa new-model
!
!
aaa group server radius rad_eap
server 192.168.2.2 auth-port 1812 acct-port 1812
!
aaa group server radius rad_mac
!
aaa group server radius rad_acct
!
aaa group server radius rad_admin
!
aaa group server tacacs+ tac_admin
!
aaa group server radius rad_pmip
!
aaa group server radius dummy
!
aaa authentication login eap_methods group rad_eap
aaa authentication login mac_methods local
aaa authorization exec default local
aaa accounting network acct_methods start-stop group rad_acct
aaa session-id common
!
dot11 ssid Admins
authentication open eap eap_methods
authentication network-eap eap_methods
authentication key-management wpa
guest-mode
!
dot11 ssid Guests
authentication open eap eap_methods
authentication network-eap eap_methods
authentication key-management wpa
guest-mode
!
power inline negotiation prestandard source
!
!
username Cisco password 7 062506324F41
!
bridge irb
!
!
interface Dot11Radio0
no ip address
no ip route-cache
!
encryption mode ciphers aes-ccm
!
ssid Guests
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role root
no dot11 extension aironet
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
!
interface Dot11Radio1
no ip address
no ip route-cache
!
encryption mode ciphers aes-ccm
!
ssid Admins
!
no dfs band block
speed basic-6.0 9.0 basic-12.0 18.0 basic-24.0 36.0 48.0 54.0
channel dfs
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
!
interface FastEthernet0
no ip address
no ip route-cache
duplex auto
speed auto
bridge-group 1
no bridge-group 1 source-learning
bridge-group 1 spanning-disabled
hold-queue 160 in
!
interface BVI1
ip address 192.168.1.2 255.255.255.0
no ip route-cache
!
ip default-gateway 192.168.1.1
ip http server
no ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
ip radius source-interface BVI1
!
radius-server attribute 32 include-in-access-req format %h
radius-server host 192.168.2.2 auth-port 1812 acct-port 1812 key 0 password
radius-server vsa send accounting
!
control-plane
!
bridge 1 route ip
!
!
!
line con 0
line vty 0 4
!
end
------------------------------------------------------------------------------------------------------------
Vyatta Router Configurations
External
1) eth0 : NAT
Internal
2) eth1 : IP address : 192.168.1.1/24
3) eth2 : IP address : 192.168.2.1/24
Configuring Vyatta
1) Now i will configure both external and internal ports in which the
external network will get it's IP address from the ISP
modem/router and the
internal networks will be configured with the address 192.168.1.1/24
and 192.168.2.1/24 (This addresses are the default gateways) . Also i am
going to allow the DHCP requests/responses from the clients and server
to pass through Vyatta router and allow the clients to get its IP
addresses.
configure
set interfaces ethernet eth0 address dhcpsource nat rule 10
source nat rule 10 outbound-interface eth0
source nat rule 10 translation address masqurade
set interfaces ethernet eth0 description Outside (optional)
set interfaces ethernet eth1 address 192.168.1.1/24
set interfaces ethernet eth1 description Servers (optional)
set interfaces ethernet eth2 address 192.168.2.1/24
set interfaces ethernet eth2 description Clients (optional)
edit service dhcp-relay
set server 192.168.2.2
set service dhcp-relay interface eth1
set service dhcp-relay interface eth2
commit
save
exit
2) Now i will check if the Ethernet ports and the relay configured correct.
show interfaces
show configuration all
**In case that you want to execute the operational mode show command(s) inside the configuration mode, just add
run in front of it.
run show interfaces
SERVERS Configurations
1) Add Roles on the server.
- 1) Active Directory Sertificate Services
- 2) Active Directory Domain Services
- 3) DHCP Server
- 4) Network Policy and Access Services
Active Directory Domain Services
1) RUN /dcpromo.exe
2) Create new domain in a new forest
3) FQDN of the forest root domain : wirelessserver.com
4) Forest Function level : Windows Server 2008 R2
DHCP SERVER
1) Select the network
2) Set the Preferred DNS Server :
Google's Public DNS :
8.8.8.8
and
IP Address of your server : 192.168.2.2
3) Add DHCP Scopes
Scope Name : wlandhcp
Starting IP Address : 192.168.1.3 (because the .1 / .2 are already assigned on the router and the AP)
Ending IP Address : 192.168.1. X (Depends on how many IP addresses you want )
Default Gateway: 192.168.1.1
Subnet Type : Wireless
RADIUS SERVER
1) Create the Wireless Users Group
- During the creation select the name of the group and the option Universal
2) Create a New User
- Add this user on the group created before.
- You can create multiple users if you want!
3) Create a New Computer
- Add this computer on the group created before
4) Configure NPS to allow the Access Point to act as a radius client.
- Select the RADIUS Server for 802.1X Wireless or Wired Connections option.
- Press Configure 802.1X
- Add the New Radius Client (Access Point )
- If you have multiple Access Points then you need to create multiple radius clients.
- Set the IP Address of the Access Point (192.168.1.2)
- Select a shared secret (e.g password) **This must be the same with the one on the Access Point's Configurations.
- Select the EAP type as Microsoft Protected EAP (PEAP)
- Specify your wireless group created before.
5) Register server in Active Directory





.bmp)
.bmp)
.bmp)
.bmp)
.bmp)
.bmp)
.bmp)
.bmp)
.bmp)
.bmp)